
Verkada for PCI Compliance
All in One System - 90-Day Video Retention, Enterprise Data Encryption & Fully Modular & Scalable
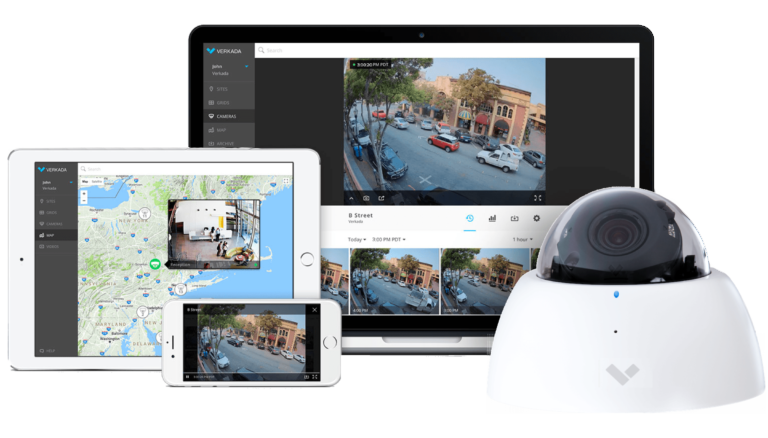
90 days of retained video - no NVRs/DVRs/servers required
Detailed user audit logs & modern data encryption standards
Configurable Smart Alerts to let admins know when something’s wrong
Background
The Payment Card Industry Data Security Standard (PCI DSS) outlines a set of requirements mandated by major credit card providers for organizations that handle their transactions. Administered by the Payment Card Industry Security Standards Council, the standard was established to strengthen protections of cardholder data and to reduce fraud.
Compliance with PCI guidelines is performed annually and, depending on the particular organization, is verified in one of three ways:
- By an external Qualified Security Assessor (QSA)
- By an Internal Security Assessor who has specific credentials for organizations handling large volumes of transactions
- By Self-Assessment Questionnaire (SAQ) - typically for organizations handling smaller volumes of transactions
About PCI Requirement 9
Updated as part of PCI DSS version 3.0, Requirement 9 outlines steps that organizations should take to restrict physical access to cardholder data. Included under this requirement are guidelines that organizations must take to limit and monitor physical access to systems in the cardholder data environment, such as points of sale (POS) systems.
PCI DSS recommends deploying entry access control mechanisms or video security cameras to meet this requirement (or both). Additionally, they require companies to:
- Verify that either video cameras or access control mechanisms (or both) are in place to monitor the entry/exit points to sensitive areas
- Verify that video cameras (or access controls) are protected from tampering or disabling
- Review collected data and correlate with other entries
- Store video data (or access logs data) for at least three months
Beyond the requirements specific to physical security, PCI DSS outlines a range of measures that organizations must take to ensure the network and data security of their facilities.
Verkada’s video surveillance technology is designed specficially to meet the high uptime and stringent data security requirements for the modern enterprise.
 Verkada Solution
Verkada Solution
Verkada offers a technology solution that simplifies the process of meeting PCI physical security requirements. Unlike traditional CCTV systems, Verkada eliminates outdated equipment such as NVRs, DVRs and on-premise servers. The result: a system design that enables modern data security standards and innovative software capabilities by default.
Product Highlights:
- No NVRs/DVRs or servers
- 90 days of on-camera video storage
- Optional cloud backup
- Motion detection and search
- Tamper detection and alerts
- Detailed user audit logs
- HTTPS/SSL data encryption (in transit)
- RSA + AES data encryption (at rest)
- Automatic firmware updates
PCI Requirement 9: Physical Security Guidelines
| PCI Requirement | Met by Verkada? | Notes |
|---|---|---|
| 9.1.1 - Use either cameras or access control, or both, in every computer room, data center and other physical areas with systems in the cardholder data environment | Unconstrained by NVRs/DVRs, Verkada systems are fully modular and scalable. You can install a single camera to cover a data closet, for example, and centrally manage 1,000s of cameras across many locations. | |
| 9.1.1.b - Ensure cameras are protected from tampering or disabling | Verkada cameras automatically detect and report tampering using physical-motion sensors and computer vision techniques. | |
| 9.2 - Develop procedures to distinguish between personnel and visitors | Verkada makes it possible to search video on motion and detect unusual or unexpected activity. Depending on your particular use case, Verkada can deploy machine learning and computer vision techniques (currently in beta) to train binary qualifiers for your system. A camera could be trained to differentiate between staff and visitors, for example, or to detect when a door is opened during off business hours. | |
| 9.3 - Control physical access for onsite personnel | Easily search recorded video to identify specifically who passing through points of ingress; review Verakda user session logs to identify which employees have accessed the system. | |
| 9.9 - Prevent tampering of payment capture devices | Tamper detection and alerts come standard for Verkada’s camera system. Beyond this, Verkada can be configured to automatically generate regular reports with recorded video of any motion that was detected at a payment capture device, such as a POS. These reports can be reviewed and action may be taken accordingly. | |
| 2.1 - Do not use vendor default passwords | Verkada systems do not have vendorprovided default passwords; SAML/Oath and 2-factor authentication, are available as standard options. | |
| 10.1 - Implement audit trails | Verkada automatically logs all user access and sessions. | |
| 10.4 - Synchronize all critical system clocks and times with timesynchronization technology | Verkada systems always have the correct date and time, using the industry-standard Network Time Protocol (NTP). | |
| 10.5 - Prevent unauthorised changes to audit logs | Verkada audit logs cannot be tampered with or altered. | |
| 10.5.3 - Audit log backup | All Verkada audit logs are backed up into geographically redundant data centers. | |
| 10.6 - Review logs and security events to identify unusual activity | Verkada enables authorised administrators to regularly review live and recorded video, as well as user sessions data, over secure connection on any device. | |
| 10.7 - Retain audit logs for 1 year | Verkada audit logs are stored securely in geographically redundant data centers and may be configured to retain data for 12 months. |

‘Zero Configuration' Setup
- No NVRs/DVRs, no VPN config, no portforwarding
- All cameras are PoE and, by default, communicate over HTTPS via port 443
- Cameras auto-provision into your account once plugged into a PoE switch with DHCP
- Automatic firmware updates keep your system secure and up to date with latest capabilities
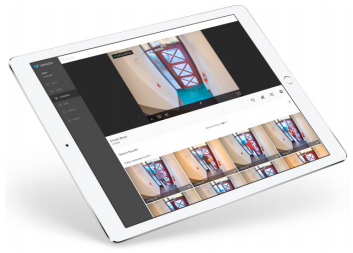
Activity Search
- Isolate areas of interest and instantly surface footage where activity was detected - e.g., pinpoint exactly when an object went missing
- Quickly export, achive and share video clips in standard formats (e.g., mp4)
- Save time, speed incident response
Real-Time Response
- Instantly share live video streams with first responders, administrators and others via SMS text and weblinks
- On-camera accelerometer sends SMS alerts when tampering is detected
- View and manage video on any device

